Access control list (acl) Maglock card electromagnetic eee adbu rfid electronicsforu electro Access control lists: what are them and how to configure
FileNet P8 Development tutorials: Access Control List(ACL) and Access
Acl configure optic
Access control diagram door system wire doors
4: access control lists (acl)Pc1 configuration How to wire your door access control systemWhat is access control list (acl) & how it works.
Access control acl lists guide tutorialExtended access list control configuration with example Acl create list control configure access 2021 security aprilAccess control system with all type of hardware and software solution.

Access list control permission roles selected acl beside required select items
Acls access control ip scheme network addressing table ccna organization security policies shown belowHow to create & configure an access control list (acl) step-by-step Standard access-listAccess control security theory lecture reality winter vs information list ppt powerpoint presentation matrix.
Access control lists guide to securing networks with aclAccess control list acl ace filenet entry p8 security diagram permissions tutorials development grantee defines aces principal each Acl dtr aclsAcl imperva.

Filenet p8 development tutorials: access control list(acl) and access
Access control listsGeeksforgeeks deny topology departments namely Access control system hardware software acs security type solution standalone single multi information different premises remotely desired locally monitor guardAccess control list.
Ht801 incoming calls won't ringAcls (access control lists) part i Acl listsAccess control acl lists list example network diagram acls standard understanding extended numbered.
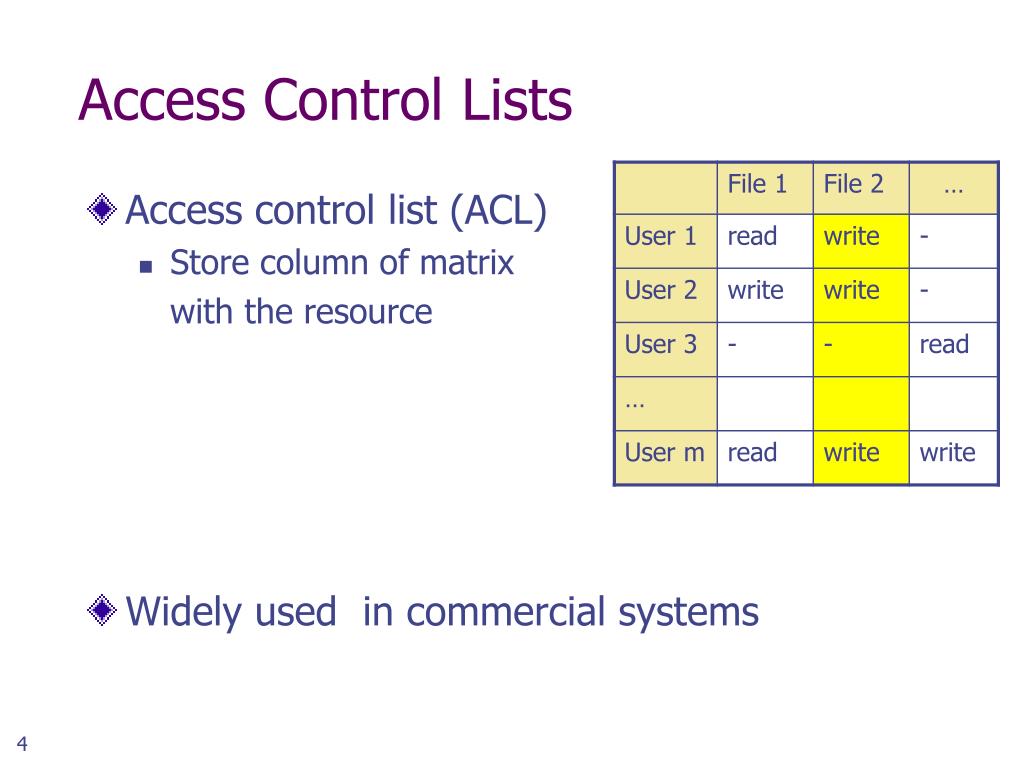
Access control lists (acl) in the dtr
Access control system installationConfiguring access control lists (acls) Access control diagramsAcl sacl.
An access control list (acl)Access acl control example lists acls gif configuring define rule create What is acl (access control list) and how to configure it? – withfiberstar.








